Authentication and Authorization with Keycloak on AWS EKS and Aurora
In today's technology landscape, managing user authentication and authorization is a critical aspect of application development. Fortunately, with the help of modern tools and cloud services, this process has become much more streamlined and efficient. In this comprehensive guide, we will explore how to leverage Keycloak, an open-source identity and access management solution, in conjunction with AWS EKS (Elastic Kubernetes Service) and AWS Aurora for PostgreSQL to simplify the management of user identities and secure access to your applications.
Understanding Keycloak
User authentication and authorization are essential components of modern applications. Keycloak is an open-source identity and access management solution that offers a wide range of features to simplify this process. It provides comprehensive support for single sign-on (SSO), social login integration, user federation, and fine-grained access control policies.
Key Features and Benefits
Keycloak offers several key features that make it a powerful choice for managing user authentication and authorization. These features include SSO capabilities, support for various identity providers, user federation for centralized user management, and flexible access control policies. Keycloak also provides integration options with other tools and frameworks, making it highly customizable and extensible.
Keycloak Architecture Overview
Keycloak follows a modular architecture that consists several components working together to provide authentication and authorization services. The Keycloak server is the central component responsible for handling user authentication, authorization, and identity management. It can be integrated with various user stores, such as databases or LDAP servers. Keycloak also supports identity brokering, which allows integration with external identity providers like Google or Facebook.
Use Cases for Keycloak
Keycloak is a versatile solution that caters to various use cases. It can be used for securing web applications, mobile applications, or microservice architectures. Keycloak's SSO capabilities enable users to log in once and access multiple applications seamlessly. Its fine-grained access control policies allow organizations to enforce authorization rules across their applications, ensuring that users only have access to the resources they are authorized for.
Setting up AWS EKS
AWS EKS (Elastic Kubernetes Service) is a managed Kubernetes service provided by Amazon Web Services. It simplifies the process of deploying, managing, and scaling containerized applications using Kubernetes.
Provisioning an EKS Cluster
Setting up an EKS cluster involves several steps, starting with creating an Amazon Virtual Private Cloud (VPC) to host the cluster. You will need to configure the VPC networking, subnets, and security groups. Once the VPC is set up, you can create the EKS cluster using the AWS Management Console, CLI, or SDKs.
Leveraging AWS Aurora for PostgreSQL
AWS Aurora for PostgreSQL is a fully managed, highly scalable, and durable relational database service provided by AWS. It offers the performance and reliability of commercial databases with the cost-effectiveness and ease of use of open-source databases.
Provisioning Aurora for PostgreSQL Cluster
To leverage Aurora for Keycloak's backend database, you need to provision an Aurora cluster. This involves selecting the appropriate instance types, storage options, and configuring the cluster settings to meet your application's requirements.
Benefits of Using Aurora for Keycloak's Backend Database
Utilizing Aurora for Keycloak's backend database brings several benefits. Aurora provides high availability, automatic scaling, and automated backups, ensuring the resilience and durability of Keycloak's data. It also offers improved performance with the ability to handle high read and write loads efficiently.
Deploying Keycloak on AWS EKS
Deployment Options: Kubernetes Manifests vs. Helm Charts
There are multiple deployment options for deploying Keycloak on EKS. One option is to use Kubernetes manifests, which define the desired state of the Keycloak deployment. Another option is to utilize Helm charts, which provide a more streamlined and automated approach for deploying Keycloak.
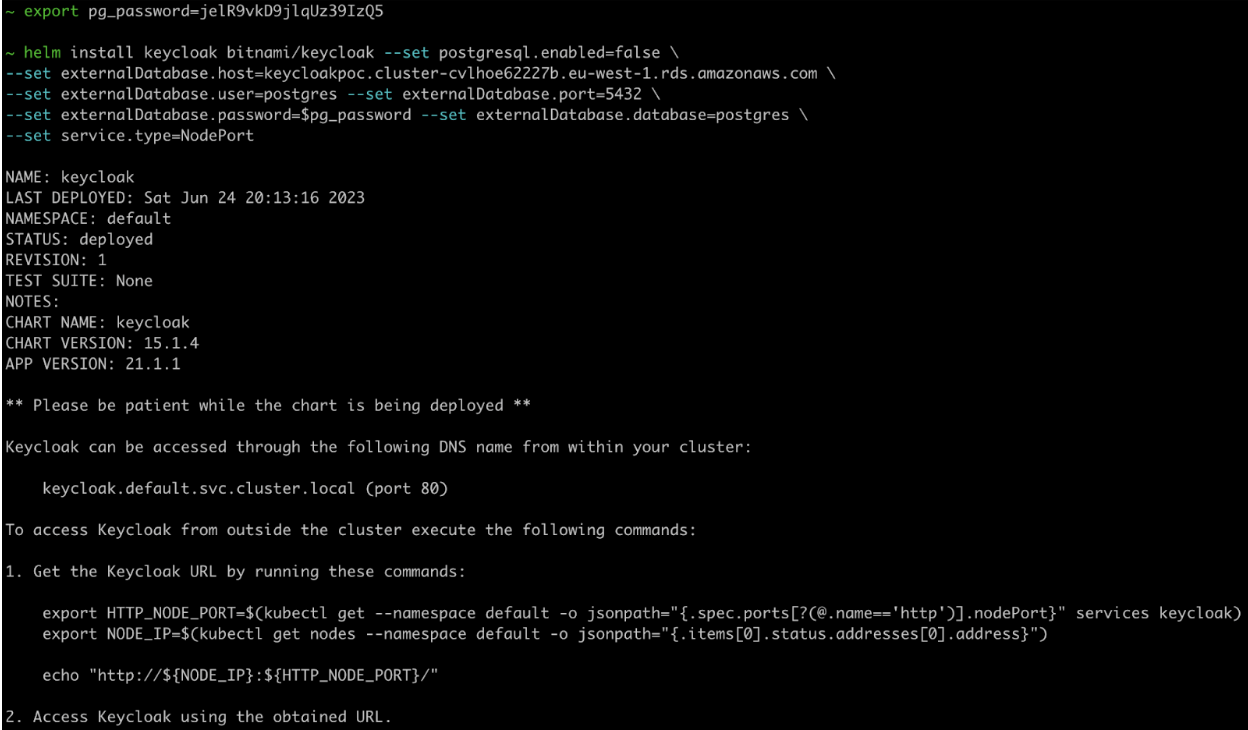
Creating Keycloak Deployment with Helm
When deploying Keycloak using Helm chart, you need to define the necessary inputs such as chart name, version, services type, and ingress rules. To ensure data persistence and scalability, it is recommended to use an external database storage solution for Keycloak. AWS Aurora for PostgreSQL is a managed database service that can be used as the backend for Keycloak.
export pg_password=
helm install keycloak bitnami/keycloak --set postgresql.enabled=false \
--set externalDatabase.host= \
--set externalDatabase.user=postgres --set externalDatabase.port=5432 \
--set externalDatabase.password=$pg_password --set externalDatabase.database=postgres \
--set service.type=NodePort
Proper management of Keycloak's lifecycle is crucial for maintaining the availability and reliability of the authentication and authorization services. This includes scaling Keycloak pods based on the workload, performing rolling updates to apply patches and updates, and monitoring Keycloak's performance and health.
Keycloak’s management console is accessible on the node port. Default admin username is user and password is in secret named keycloak.
Securing Access to Applications
Keycloak follows a standardized authentication and authorization flow. Understanding this flow is crucial for implementing secure access to applications integrated with Keycloak.
Implementing Single Sign-On (SSO) with Keycloak
Keycloak provides robust support for implementing SSO across multiple applications. By configuring Keycloak as an identity provider, users can log in once and access multiple applications without having to provide their credentials again.
Keycloak offers integration with popular social identity providers such as Google, Facebook, and Twitter. This enables users to log in to Keycloak using their social media accounts, simplifying the registration and login process.
Implementing Fine-Grained Access Control Policies
Keycloak's fine-grained access control policies allow organizations to define granular authorization rules. By assigning roles and permissions, access to resources within applications can be controlled with precision.
Conclusion
By combining the power of Keycloak, AWS EKS, and AWS Aurora for PostgreSQL, you can simplify the management of user authentication and authorization in your applications. Keycloak's rich feature set, combined with the scalability and reliability of AWS services, provide a robust foundation for securing access to your applications. With detailed explanations and step-by-step instructions provided in this guide, you will have the knowledge and tools necessary to successfully deploy and configure Keycloak on AWS EKS and integrate it with AWS Aurora for PostgreSQL. Embrace the power of these technologies to enhance the security and user experience of your applications.
Ahmet Aydın
Senior DevOps Consultant @kloia

