LigaBet is a well-known gaming company and their efforts are focused at growing the betting industry, promoting and producing new forms of entertainment.
LigaBet wanted to serve their customers globally and they’ve decided to migrate all of their workloads to AWS with kloia’s partnership. We are going through an AWS Migration Acceleration Program with them and this case study reflects on our progress.
Problem
AWS MAP projects tend to have extensive scope and various domains of task to be executed. The most important ones emerge from migrating to new infrastructure, and at the same time, wanting to make the most out of available AWS services.
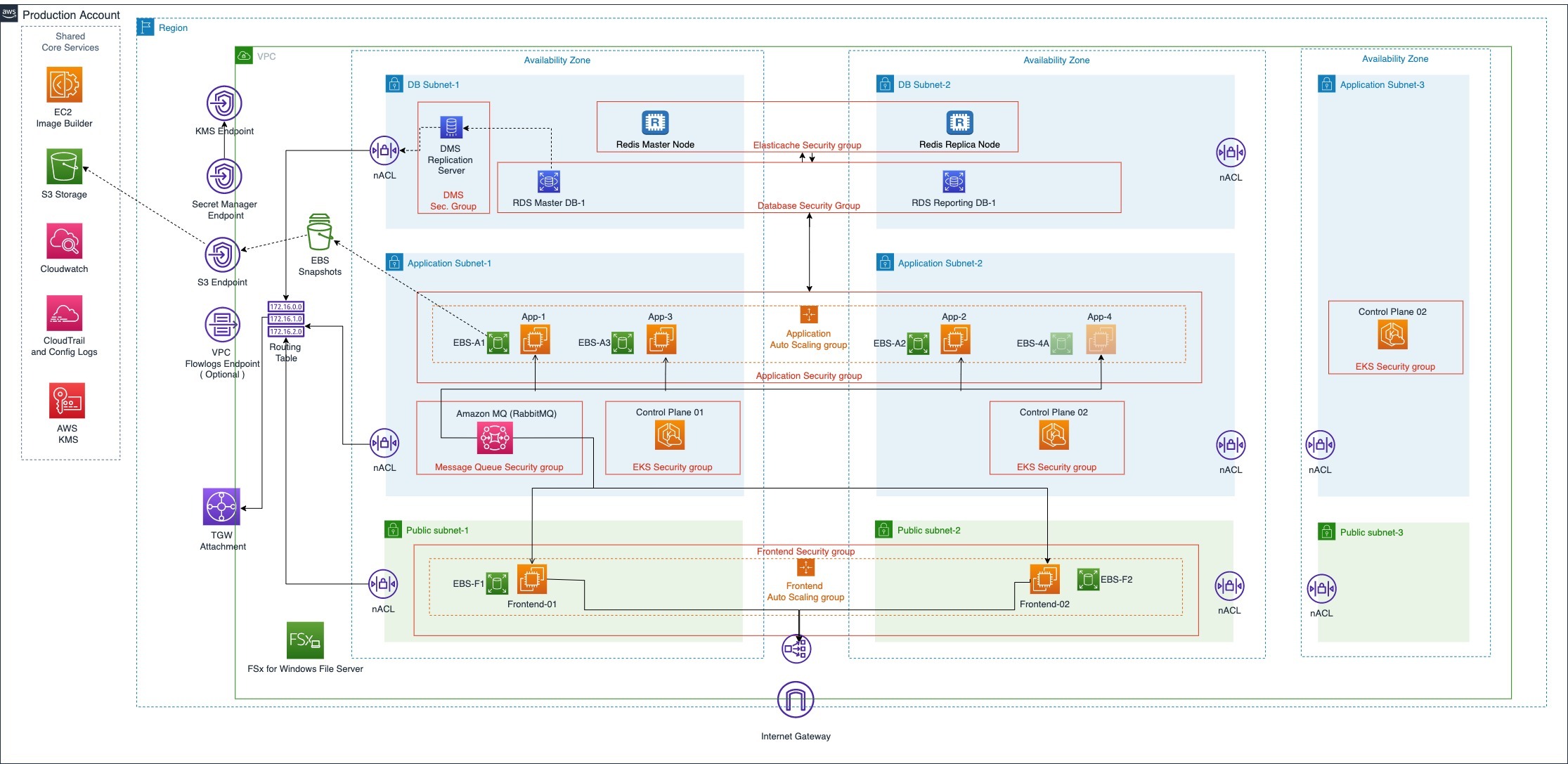
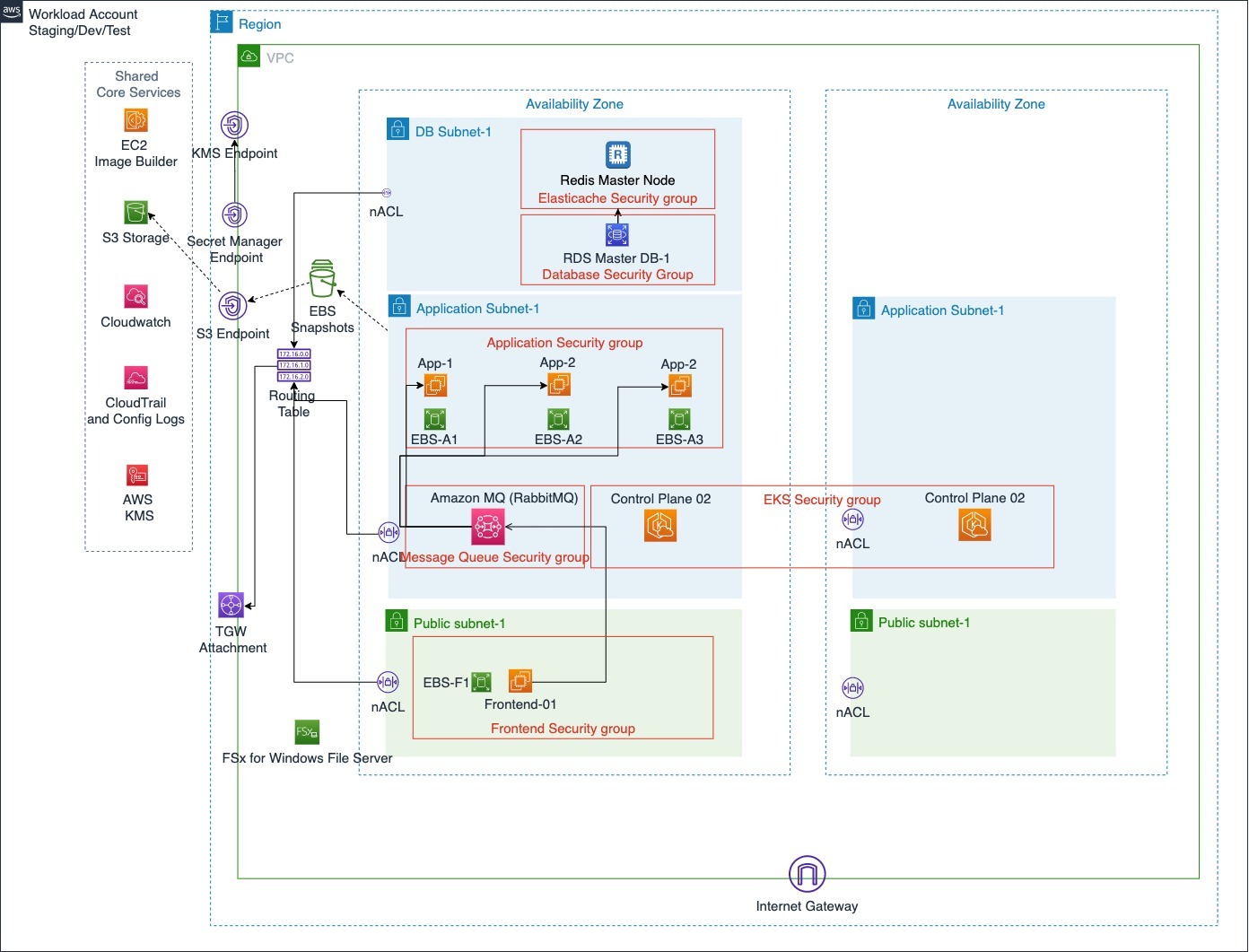
LigaBet’s AWS Migration journey was extensive in scope, and its main requirement dictated a Multi-Account strategy and usage of AWS Organizations. This main requirement can be described as the automated capability of adding and removing the environment infrastructure (dev, production, etc.) as a separate AWS Account.
The AWS Organization contains Shared* accounts for centralized Logging, Security and Networking. This architecture supports adding arbitrary numbers of Workload Accounts because they’d only have to run the applications.
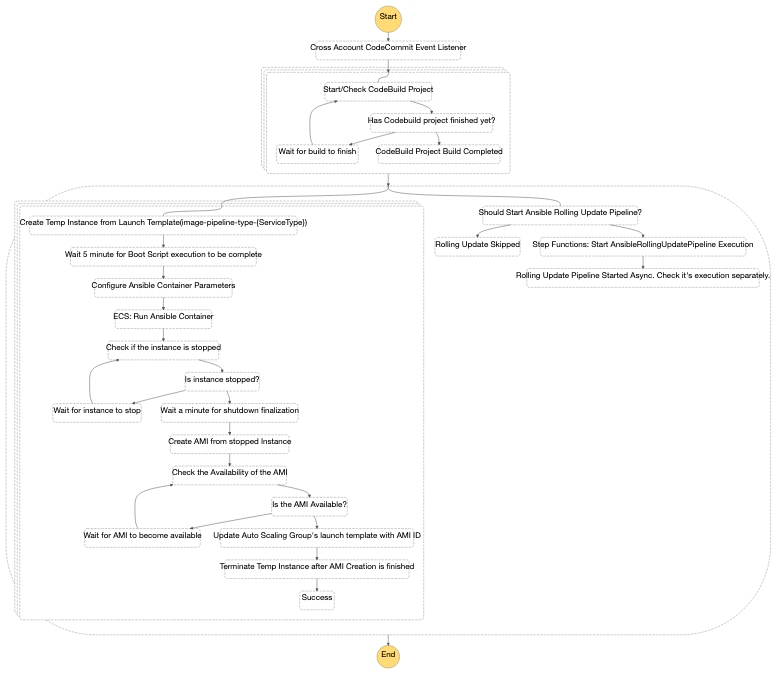
Migrating highly cohesive legacy Windows applications has prompted a new issue: CI/CD pipelines. LigaBet’s requirements made it very hard to use 3rd party, off-the-shelf pipeline tools. We’ve created an in-house serverless CI/CD pipeline with Step Functions that follows the GitOps principles.
Client: LigaBet
Project type: Migration to AWS
Website: LigaBet
.webp?width=1478&quality=low)